
Concord has launched its all-new AI native platform, Horizon!

Concord has launched its all-new AI native platform, Horizon!

Concord has launched its all-new AI native platform!
Security & Compliance
Security & Compliance
Security & Compliance

Concord provides a SOC 2 type II report. This report can be accessed through our Conveyor portal.

Concord values your privacy. You can choose where your data is stored, and also have the option to enter into a Data Processing Agreement.

Concord has received a Star Level One rating from the Cloud Security Alliance — the highest transparency rating.

Concord’s servers are hosted on AWS, in compliance with SOC 1, SOC 2, SOC 3, ISO 27x, FedRamp, PCI DSS, HIPAA, FIPS, FISMA, and CSA.

The DPF enables U.S. organizations to transfer personal data from the EU, UK, and Switzerland in line with privacy laws. Concord is certified under the EU-U.S. DPF and its UK and Swiss extensions.

Concord provides a SOC 2 type II report. This report can be accessed through our Conveyor portal.

Concord values your privacy. You can choose where your data is stored, and also have the option to enter into a Data Processing Agreement.

Concord has received a Star Level One rating from the Cloud Security Alliance — the highest transparency rating.

Concord’s servers are hosted on AWS, in compliance with SOC 1, SOC 2, SOC 3, ISO 27x, FedRamp, PCI DSS, HIPAA, FIPS, FISMA, and CSA.

The DPF enables U.S. organizations to transfer personal data from the EU, UK, and Switzerland in line with privacy laws. Concord is certified under the EU-U.S. DPF and its UK and Swiss extensions.

Concord provides a SOC 2 type II report. This report can be accessed through our Conveyor portal.

Concord values your privacy. You can choose where your data is stored, and also have the option to enter into a Data Processing Agreement.

Concord has received a Star Level One rating from the Cloud Security Alliance — the highest transparency rating.

Concord’s servers are hosted on AWS, in compliance with SOC 1, SOC 2, SOC 3, ISO 27x, FedRamp, PCI DSS, HIPAA, FIPS, FISMA, and CSA.

The DPF enables U.S. organizations to transfer personal data from the EU, UK, and Switzerland in line with privacy laws. Concord is certified under the EU-U.S. DPF and its UK and Swiss extensions.
Application Security
Application Security
Application Security
Concord stores all content in geographically dispersed, ISO 27001-certified and SSAE 16-audited, data centers throughout the United States and Europe. These data centers include state-of-the-art physical and environmental access controls and safety features.
All data in Concord is encrypted in transit and at rest. We use TLS 1.2 or higher for data in transit, and banking industry standard AES-256 encryption for data at rest.
Concord employees only have access to customer data on a strict need-to-know basis. Customers have granular access management with complex passwords, SSO, and two-factor authentication (2FA).
Concord uses redundant geo-dispersed servers; we can adjust their capabilities in real-time depending on the current load. In addition to data replication, automated full daily backups prevent any data loss. All backups are encrypted.
Concord’s infrastructure provides security and application monitoring and alerts. Concord has a strict incident management policy in place, in case of a critical alert.
Concord performs bi-annual external penetration testing as well as a daily internal scan. Concord follows SDLC principles, and addresses any identified vulnerabilities based on a well-defined vulnerability management policy.
Concord only uses third-party subprocessors after performing careful due diligence. We perform an annual review of all our subprocessors.
Concord uses a PCI Data Security Standard (PCI DSS) Level 1 provider to process payments. PCI Data Security Standard (PCI DSS), to maintain a secure environment.
Concord’s Agreement Intelligence enables automated extraction of key information with AI. Concord’s AI provider has signed an agreement that requires them to adhere to a zero data retention policy. No customer data is used for AI model training.
Concord stores all content in geographically dispersed, ISO 27001-certified and SSAE 16-audited, data centers throughout the United States and Europe. These data centers include state-of-the-art physical and environmental access controls and safety features.
All data in Concord is encrypted in transit and at rest. We use TLS 1.2 or higher for data in transit, and banking industry standard AES-256 encryption for data at rest.
Concord employees only have access to customer data on a strict need-to-know basis. Customers have granular access management with complex passwords, SSO, and two-factor authentication (2FA).
Concord uses redundant geo-dispersed servers; we can adjust their capabilities in real-time depending on the current load. In addition to data replication, automated full daily backups prevent any data loss. All backups are encrypted.
Concord’s infrastructure provides security and application monitoring and alerts. Concord has a strict incident management policy in place, in case of a critical alert.
Concord performs bi-annual external penetration testing as well as a daily internal scan. Concord follows SDLC principles, and addresses any identified vulnerabilities based on a well-defined vulnerability management policy.
Concord only uses third-party subprocessors after performing careful due diligence. We perform an annual review of all our subprocessors.
Concord uses a PCI Data Security Standard (PCI DSS) Level 1 provider to process payments. PCI Data Security Standard (PCI DSS), to maintain a secure environment.
Concord’s Agreement Intelligence enables automated extraction of key information with AI. Concord’s AI provider has signed an agreement that requires them to adhere to a zero data retention policy. No customer data is used for AI model training.
Concord stores all content in geographically dispersed, ISO 27001-certified and SSAE 16-audited, data centers throughout the United States and Europe. These data centers include state-of-the-art physical and environmental access controls and safety features.
All data in Concord is encrypted in transit and at rest. We use TLS 1.2 or higher for data in transit, and banking industry standard AES-256 encryption for data at rest.
Concord employees only have access to customer data on a strict need-to-know basis. Customers have granular access management with complex passwords, SSO, and two-factor authentication (2FA).
Concord uses redundant geo-dispersed servers; we can adjust their capabilities in real-time depending on the current load. In addition to data replication, automated full daily backups prevent any data loss. All backups are encrypted.
Concord’s infrastructure provides security and application monitoring and alerts. Concord has a strict incident management policy in place, in case of a critical alert.
Concord performs bi-annual external penetration testing as well as a daily internal scan. Concord follows SDLC principles, and addresses any identified vulnerabilities based on a well-defined vulnerability management policy.
Concord only uses third-party subprocessors after performing careful due diligence. We perform an annual review of all our subprocessors.
Concord uses a PCI Data Security Standard (PCI DSS) Level 1 provider to process payments. PCI Data Security Standard (PCI DSS), to maintain a secure environment.
Concord’s Agreement Intelligence enables automated extraction of key information with AI. Concord’s AI provider has signed an agreement that requires them to adhere to a zero data retention policy. No customer data is used for AI model training.
Product Security
Product Security
Product Security
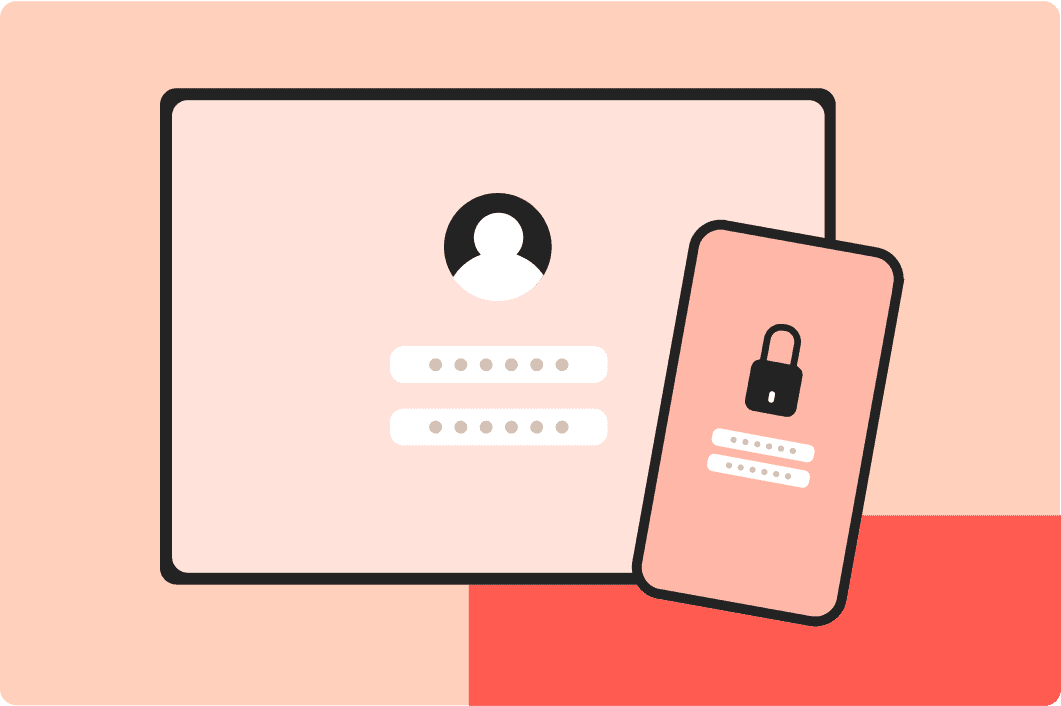
Identity & 2FA
In Concord, administrators can create as many users roles and categories as are required by their organization’s workflow. Admins can grant rights on a feature-by-feature basis, and control the types of documents that each user can view — ensuring that only authorized individuals can access designated contracts, or confidential and sensitive documents, while admins maintain granular control over their data. You can set up SSO and 2FA for your employees.

Identity & 2FA
In Concord, administrators can create as many users roles and categories as are required by their organization’s workflow. Admins can grant rights on a feature-by-feature basis, and control the types of documents that each user can view — ensuring that only authorized individuals can access designated contracts, or confidential and sensitive documents, while admins maintain granular control over their data. You can set up SSO and 2FA for your employees.

Identity & 2FA
In Concord, administrators can create as many users roles and categories as are required by their organization’s workflow. Admins can grant rights on a feature-by-feature basis, and control the types of documents that each user can view — ensuring that only authorized individuals can access designated contracts, or confidential and sensitive documents, while admins maintain granular control over their data. You can set up SSO and 2FA for your employees.
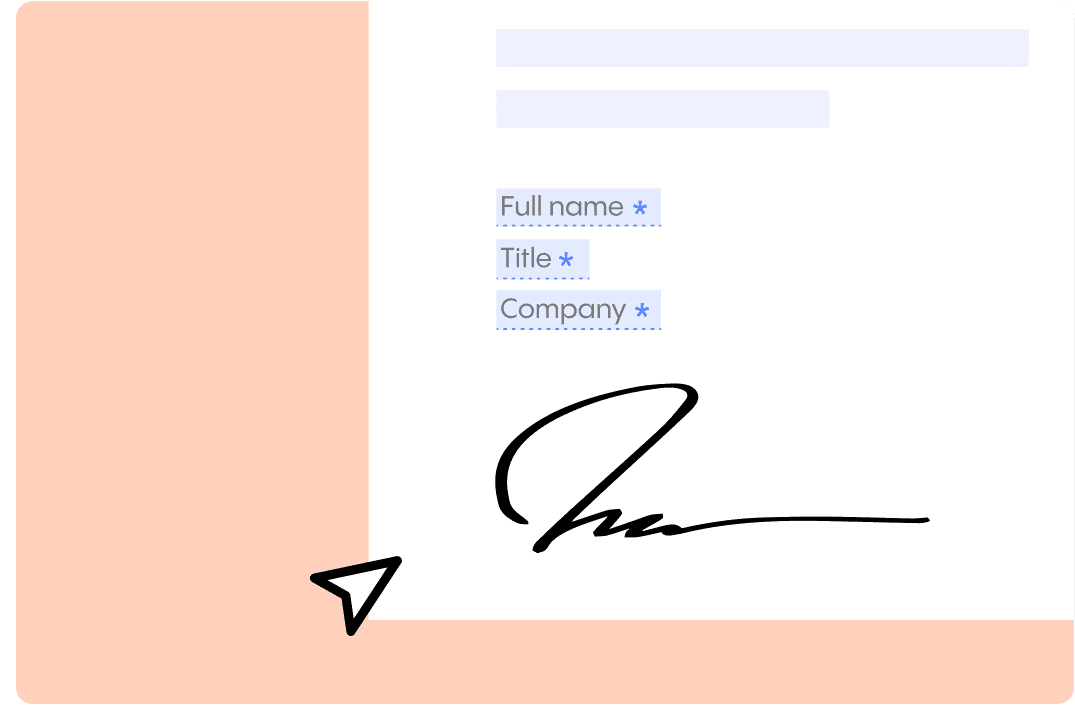
Signature
Concord’s e-signatures comply with eIDAS, UETA and the eSign Act. Our e-signatures are legal in more than 150 countries (and counting), and comply with regulations throughout the world. After you sign a document, you can easily download an e-signature certificate that will be valid forever. See more information here.

Signature
Concord’s e-signatures comply with eIDAS, UETA and the eSign Act. Our e-signatures are legal in more than 150 countries (and counting), and comply with regulations throughout the world. After you sign a document, you can easily download an e-signature certificate that will be valid forever. See more information here.

Signature
Concord’s e-signatures comply with eIDAS, UETA and the eSign Act. Our e-signatures are legal in more than 150 countries (and counting), and comply with regulations throughout the world. After you sign a document, you can easily download an e-signature certificate that will be valid forever. See more information here.
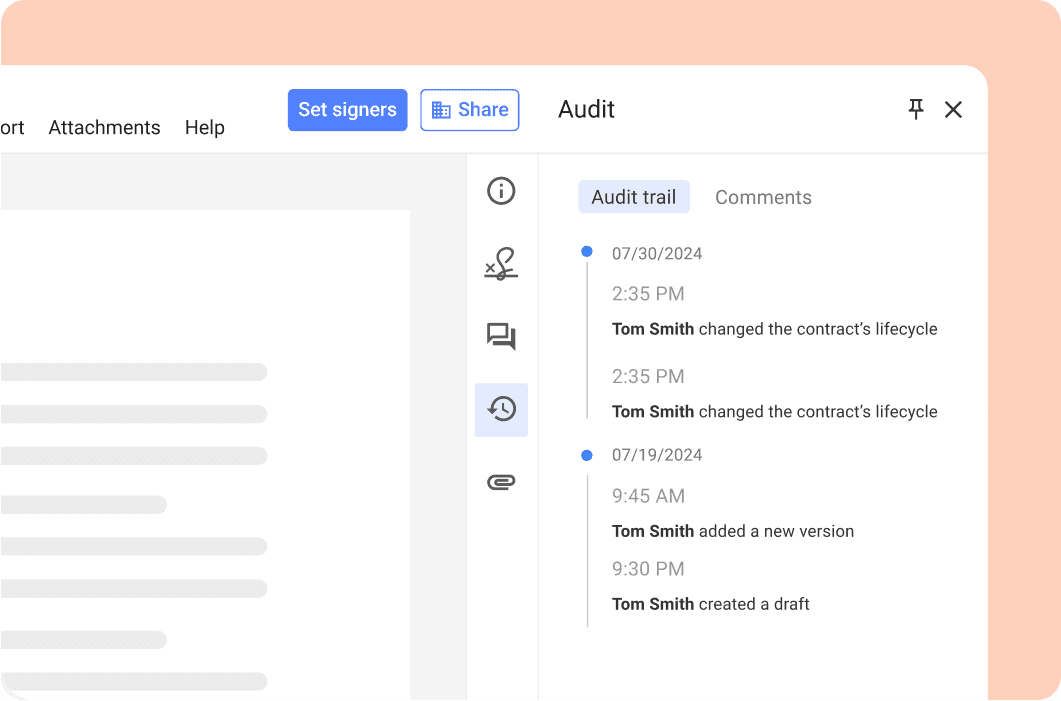
Audit trail
The audit trail logs all of the activity that occurs in a document, including the date, time, and the person who performed each action. It will continue to record actions taken in a document even after it has been signed. This includes invitations, changes to the lifecycle dates, and termination of the document. The audit trail and documents cannot be tampered with. This will be particularly important if you ever have to present court-admissible evidence.

Audit trail
The audit trail logs all of the activity that occurs in a document, including the date, time, and the person who performed each action. It will continue to record actions taken in a document even after it has been signed. This includes invitations, changes to the lifecycle dates, and termination of the document. The audit trail and documents cannot be tampered with. This will be particularly important if you ever have to present court-admissible evidence.

Audit trail
The audit trail logs all of the activity that occurs in a document, including the date, time, and the person who performed each action. It will continue to record actions taken in a document even after it has been signed. This includes invitations, changes to the lifecycle dates, and termination of the document. The audit trail and documents cannot be tampered with. This will be particularly important if you ever have to present court-admissible evidence.
Customer Support
Legal
Compare
Resources
Customer Support
Company
Legal
Compare
Resources
Customer Support
Company
Legal
Compare
© 2025 Concord. All rights reserved.





